wannacry package download test|wannacry download zip : trading Projects - GitHub - limiteci/WannaCry: this repository contains the active DOS . 8 de jul. de 2023 · A construção da Barragem do Engenho Pereira seria a solução, juntamente com medidas de desassoreamento da calha do rio e dos diversos canais que se conectam com o Jaboatão. Outro desafio é .
{plog:ftitle_list}
19/10/2023 04h00 Atualizado há 3 meses. Palmeiras e Atlético-MG se enfrentam nesta quinta-feira, às 19h (de Brasília), no Allianz Parque, em São Paulo, pela 27ª rodada do Campeonato Brasileiro. O Premiere transmite a partida ao vivo e o ge acompanha em Tempo Real, com vídeos dos principais lances (clique aqui para seguir).
this repository contains the active DOS/Windows ransomware, WannaCry. ⚠️ WARNING ⚠️ running this .exe file will damage your PC, use a secure burner VM / VirtualBox to test it. link .this repository contains the active DOS/Windows ransomware, WannaCry .Welcome to pull requests! Pull requests help you collaborate on code with other .Save time with matrix workflows that simultaneously test across multiple .
Projects - GitHub - limiteci/WannaCry: this repository contains the active DOS .GitHub is where people build software. More than 100 million people use .
Insights - GitHub - limiteci/WannaCry: this repository contains the active DOS .6 Commits - GitHub - limiteci/WannaCry: this repository contains the active DOS .this repository contains the active DOS/Windows ransomware, WannaCry .
Activity - GitHub - limiteci/WannaCry: this repository contains the active DOS .1 Branch - GitHub - limiteci/WannaCry: this repository contains the active DOS .
malware-samples. A collection of malware samples caught by . Test for applicable patches to prevent the WannaCry malware. Tests for SMB1 protocol and component. Installation Options WannaCry (also known as WCry or WanaCryptor) malware is a self-propagating (worm-like) ransomware that spreads through internal networks and over the public internet by .
This fact sheet provides information on how the WannaCry program spreads, what users should do if they have been infected, and how to protect against similar attacks in the . WannaCry is a ransomware crypto-worm that targets computers running the Windows operating system by encrypting data and demanding ransom payments. The worm is also known as WannaCrypt, Wanna. One infamous piece of malware that wreaked havoc in 2017 is WannaCry ransomware. In this blog post, we will walk through the process of analyzing WannaCry, both statically and dynamically, to.
WannaCry (aka WCry or WanaCryptor) malware is self-propagating (worm-like) ransomware that spreads through internal networks and over the public internet by exploiting a vulnerability in. Use PowerShell to help test and resolve issues from WannaCry / WannaCrypt variants and other ransomware attacks.this repository contains the active DOS/Windows ransomware, WannaCry. ⚠️ WARNING ⚠️ running this .exe file will damage your PC, use a secure burner VM / VirtualBox to test it. link . "WannaCry doesn't seem to have a way of associating a payment to the person making it." Bossert echoed that today, saying that approximately ,000 had been paid out since Friday, but there's no .
To the maximum extent permitted by applicable law, I shall not be held liable for any indirect, incidental, special, consequential or punitive damages, or any loss of profits or revenue, whether incurred directly or indirectly, or any loss of data, use, goodwill, or other intangible losses, resulting from (i) your access to this resource and/or inability to access this .
Based on our analysis, malicious binaries associated with WannaCry activity are comprised of two distinct components, one that provides ransomware functionality – acting very similar to WannaCry malware samples . Download link. Windows Server 2003 SP2. 4012598 5.2.3790.6021. Windows Server 2003 SP2 x64 Windows Server 2003 SP2 x86. Windows XP. 4012598 5.1.2600.7208. Windows XP SP2 x64 Windows XP SP3 x86 Windows XP Embedded SP3 x86. Windows Vista SP2. 4012598 GDR:6.0.6002.19743 LDR:6.0.6002.24067. Windows Vista Service Pack 2 .
WannaCry was the biggest ransomware attack in history it was diffrent than any other ransomeware as it could spread through the local network by its own by exploiting the SMB Vulnerability. But a kill switch was discovered by British security researcher Marcus Hutchins, who stopped the attack by registering the web domain found in the malware . Boot the virtual machine back up and double click on the Ransomware.WannaCry.zip file on the Desktop and unzip the EXE that is contained inside. The password for unzipping is on the GitHub download page. Then simply double click on the EXE to start WannaCry and watch the carnage.You signed in with another tab or window. Reload to refresh your session. You signed out in another tab or window. Reload to refresh your session. You switched accounts on another tab or window.
wannacry sample download
What is WCry ransomware? WannaCry, sometimes also called WCry or WanaCryptor is ransomware malware, meaning that it encrypts files of its victims and demands a payment to restore the stolen information, usually in bitcoin with ransom amounts ranging from 0 to 0 equivalents.. The virus can be described as ransomware like Dharma or Ryuk but with worm . Instead — if you're able to — download and install Microsoft patch MS17-010, available here, which should work on Windows systems going all the way back to Vista. Alex Johnson Fig.4. Can see windows binary like ‘icals’ and the command ‘attrib +h .’ suggests that it has some hidden directory somewhere!. Now moving on Open ‘PE Studio’ and load the binary into .
Why was WannaCry so successful? Ransomware like WannaCry typically works by encrypting your files or locking your system. It then demands payment in the shape of a cryptocurrency like Bitcoin because such currencies are more complex to trace than electronic money transfers, checks, or cold hard cash.
Analyse suspicious files, domains, IPs and URLs to detect malware and other breaches, automatically share them with the security community. How was WannaCry’s spread stopped in 2017? The 2017 WannaCry ransomware campaign was stopped almost by a total fluke. Two security researchers, Marcus Hutchens and Jamie Hankins, discovered a web address in WannaCry’s code and, realizing that it was unregistered, quickly claimed it.test/fix if you are safe from viruses WannaCrypt/WannaCry whatever it is - akbaryahya/WannaCrypt-Detection . Automate any workflow Packages. Host and manage packages Security. Find and fix vulnerabilities Codespaces. Instant dev environments GitHub Copilot. Write better code with AI Code review. Manage code changes Issues. Plan and track . I HAVE CHANNEL MEMBERSHIPS NOW!!Check out WIPs, previews, and updates on my songs, with some other extra stuff in there too :3Join here:https://www.youtube.c.
WannaCry and NotPetya, probably two most damaging cyberattacks in recent history, were both only made possible because of EternalBlue. . The Metasploit Framework contains a suite of tools that you .virus malware trojan rat ransomware spyware malware-samples remote-admin-tool malware-sample wannacry remote-access-trojan emotet loveletter memz joke-program emailworm net-worm pony-malware loveware ethernalrocks Resources. Readme Activity. Stars. 1.1k stars Watchers. 49 watching Forks. 240 forks Report repository Releases No releases . WannaCry worked in the same way as most ransomware. It targeted Microsoft Windows operating systems, encrypting the user's data and demanding payment. Upon attack it would demand a payment ranging from 0 to 0 in the form of bitcoin. WannaCry threatened its victims by promising to delete all user files if the ransom went unpaid for three days.Click Launch to launch RanSim or double-click the KnowBe4 Ransomware Simulator icon on your desktop.. Click the Check Now button to start RanSim's simulations. After clicking, RanSim will run 21 separate infection scenarios which will simulate different types and methods of ransomware. It will also run two "false positive" scenarios, which your antivirus should allow to .
WannaCry attacks are initiated using an SMBv1 remote code execution vulnerability in Microsoft Windows OS. The EternalBlue exploit has been patched by Microsoft on March 14 and made publicly available through the "Shadowbrokers dump" on April 14th, 2017. However, many companies and public organizations have not yet installed the patch to their . What is WannaCry Ransomware. WannaCry (also referred to as Wcry, Wana Decrypt0r 2.0, WanaDecryptor, and WNCRY virus) is a ransomware infection that encrypts personal files using AES-128 algorithms and demands victims to pay for decryption.The virus was discovered by a security researcher S!Ri and there are a couple of known WannaCry variants. .
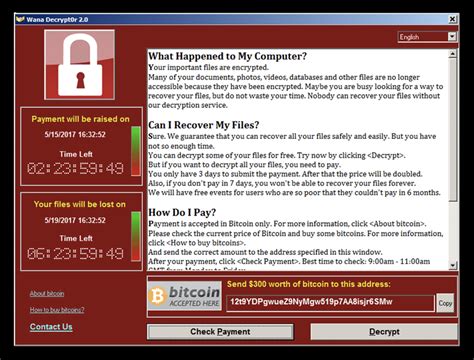
The core of WannaCry is a vulnerability in a Windows file-sharing system called SMB, which allowed WannaCry to spread quickly across vulnerable systems with no user interaction. But when Kryptos .
If your PC has been infected by WannaCry – the ransomware that wreaked havoc across the world last Friday – you might be lucky to get your locked files back without paying the ransom of 0 to the cyber criminals. Adrien Guinet, a French security researcher from Quarkslab, has discovered a way to retrieve the secret encryption keys used by the .WannaCry (WCRY) {Original file name}.WNCRY, {Original file name}.WCRY: Petya: . Obtaining and Executing the Tool(s) Click the Download button below to obtain the latest version of the Trend Micro Ransomware File Decryptor tool. Decompress (unzip) and then launch the included RansomwareFileDecryptor exe file. . V2 decryption tool now is in a . WannaCry FAQ: How does WannaCry spread? WannaCry has multiple ways of spreading. Its primary method is to use the Backdoor.Double.Pulsar backdoor exploit tool released last March by the hacker group known as Shadow Brokers, and managed to infect thousands of Microsoft Windows computers in only a few weeks. Because DoublePulsar runs .
No shit, but Wannacry wasn't just an MS17-010 exploit, it was a full malware package with ransomware. The ransomware doesn't use MS17-010 to install itself, it uses MS17-010 to spread. But thanks for proving my point. The Primes extraction method is based on Adrien Guinet's wannakey which consist of scanning the WannaCry process memory to recover the prime numbers that were not cleaned during CryptReleaseContext(). Adrien's method was originally described as only valid for Windows XP but @msuiche and I proved this can be extended to Windows 7.
brix refractometer homebrew
brix refractometer honey
Resultado da 11 de jun. de 2011 · Beto Barbosa e Sucesso !!!Ai que coisa boa, ai que coisa Louca, Você me amando dizendo mais, E na onda do bole bole, e do mexe .
wannacry package download test|wannacry download zip